- Picked up a few of these outdoor wireless remote control outlets over the past few weeks. They are not bluetooth or wifi and seem to be operate like a garage door opener with and
onandoffbuttonDevice Info
- Model: UTTNOREM2 (0357410) Plug-in remote control
- FCC ID: QJXTNOREM02
- Model: UTTNOREM2 (T-001) Battery Powered Remote
- FCC ID: QJXT-001
Acquisition
- I picked up 3x of these over the past few weeks from the local return auction. Two came with both the plug and transmitter but one only had the outlet plug
- Overall, spent only about $15.00 for the three of them which is a good deal considering brand new they are around $12-15 each
FCC lookup
- Loking up the FCC ID online
- Internal photos from FCC database
- Do not see any modern style IOT chipset
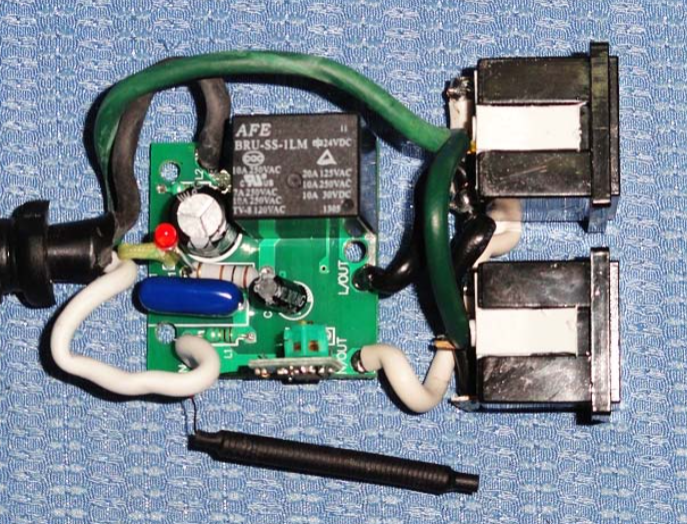
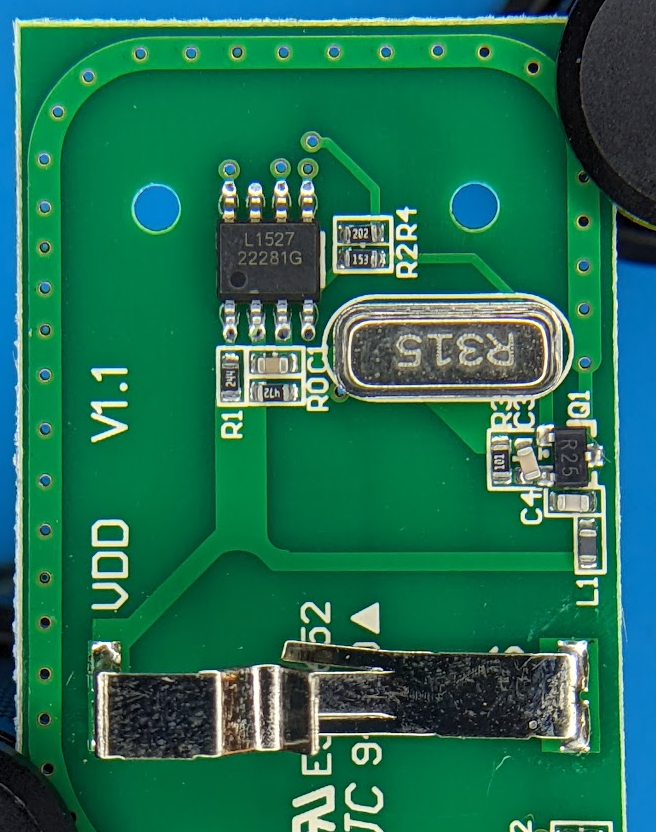
- Out of the case
- Looks like this little PCB has the antenna and most likely A/D signal processing
Transmitter
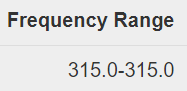
- No internal photos on FCC site
- Has frequency range on the FCC application
- Opened one of the transmitters up to take a look inside. Powered by a CR2032 3V battery
Wireless Exploits
- Seems like a good target to try to capture the RF signal at 315MHZ and try to do a replay attack and also figure out the coding
- The transmitters are paired with the outlets by pressing both
onandoffsimultaneously in the first 10-15 secs of the outlets being powered on - I beleive this means the transmitter holds the magic and generates the unique parameters for the outlets to accept and then store in memory to listen for
onandofftriggers - The outlets can be paired with both transmittters labeled as
0323and0623- Assuming those numbers might come up during analysis of the signals and unique identifiers….
HackRF One
- Using my Aliexpress knockoff HackRF One
Universal Radio Hacker
- Download latest release of Universal Radio Hacker
- Record the on and off signals from the 0323 transmitter
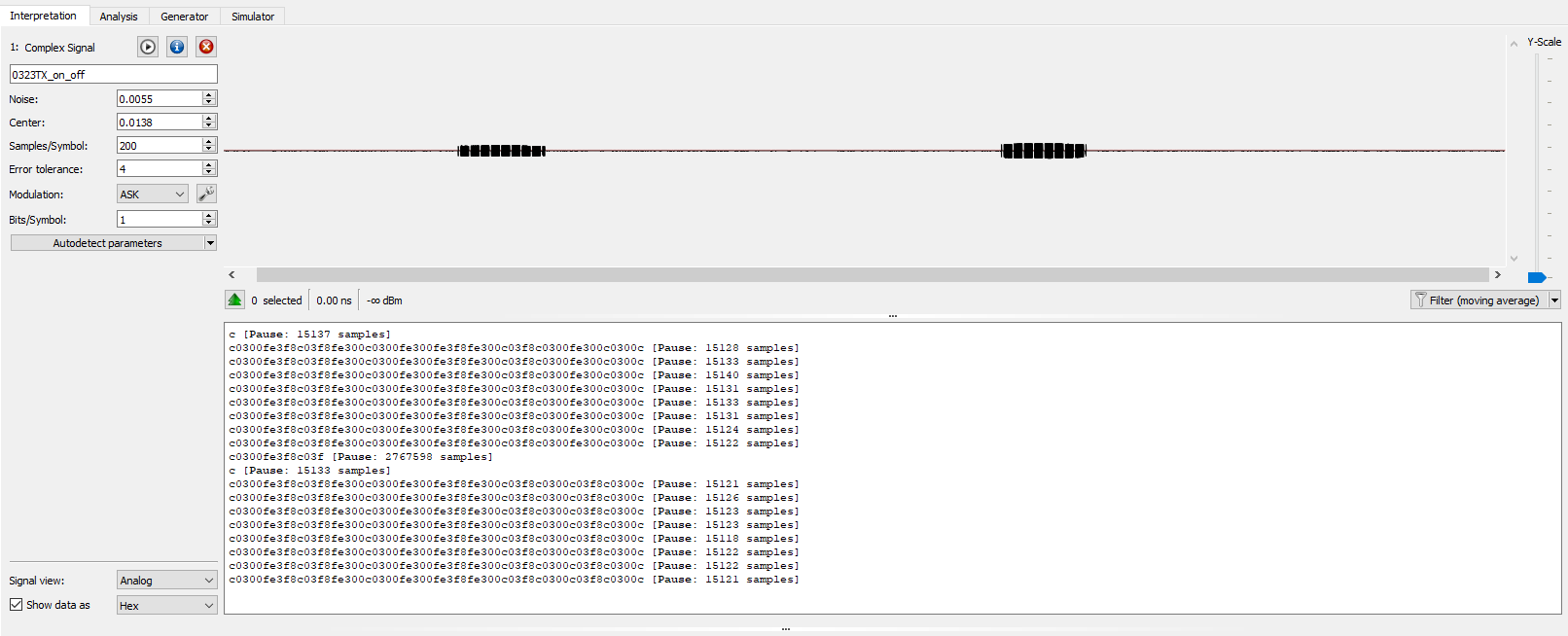
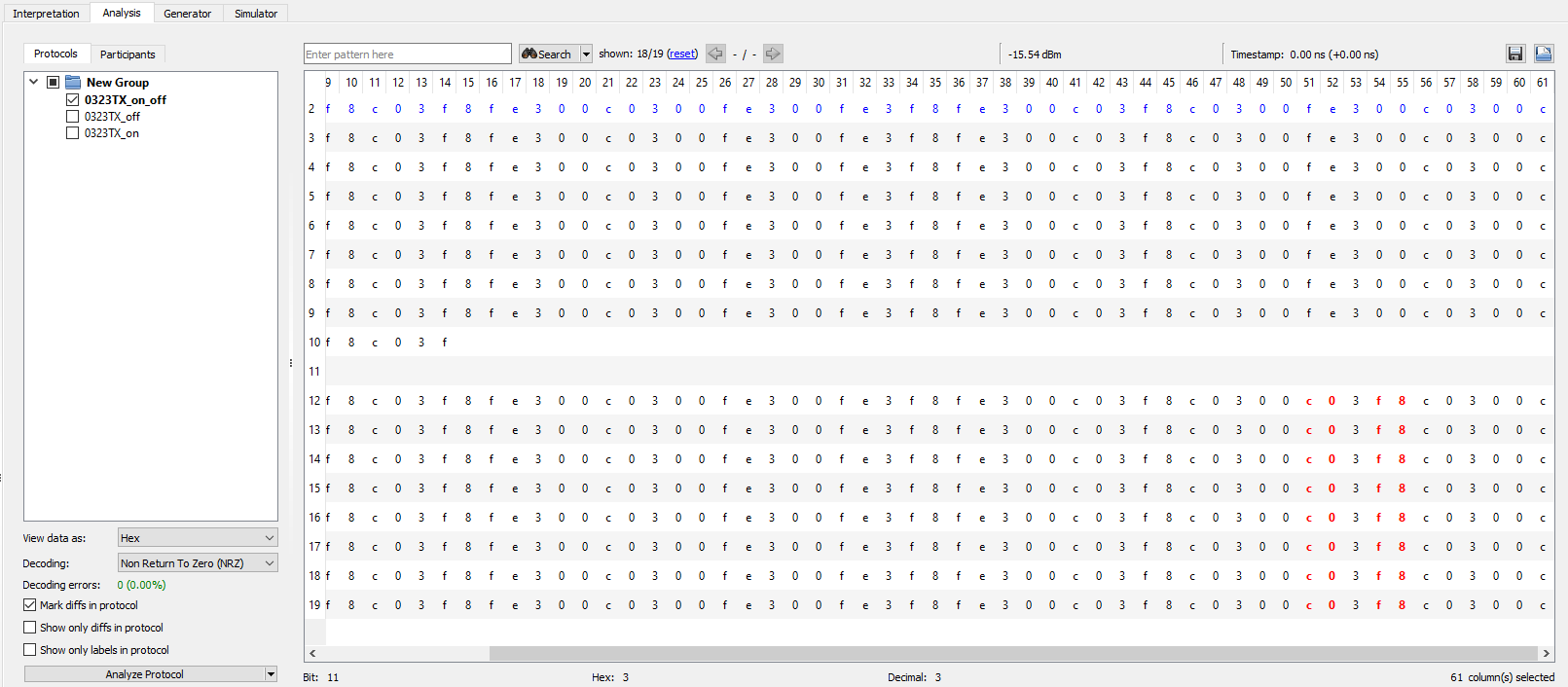
Analysis - Interpretation Tab
- Interpretation tab shows the signal just captured
- Can leverage the
Autodetect parametersfunctionality of URH and let it do some guessing for us - Initial parameter guess assigned it as an
Amplitude Shift Keysignal with 1400 samples/symbol… which seems off - Zooming in on one message block, there appears to be 25 messages that are repeated for both
onandoff
- Using some made up logic (maybe it’s correct) and assuming some factor of
8the Samples/Symbol is set to 200 (25x8) and the data viewed in hex cleans up nicely
- On Message »
c0300fe3f8c03f8fe300c0300fe300fe3f8fe300c03f8c0300fe300c0300c - Off Message »
c0300fe3f8c03f8fe300c0300fe300fe3f8fe300c03f8c0300c03f8c0300c - Quick visual comparison and only 5 symbols are different between the two
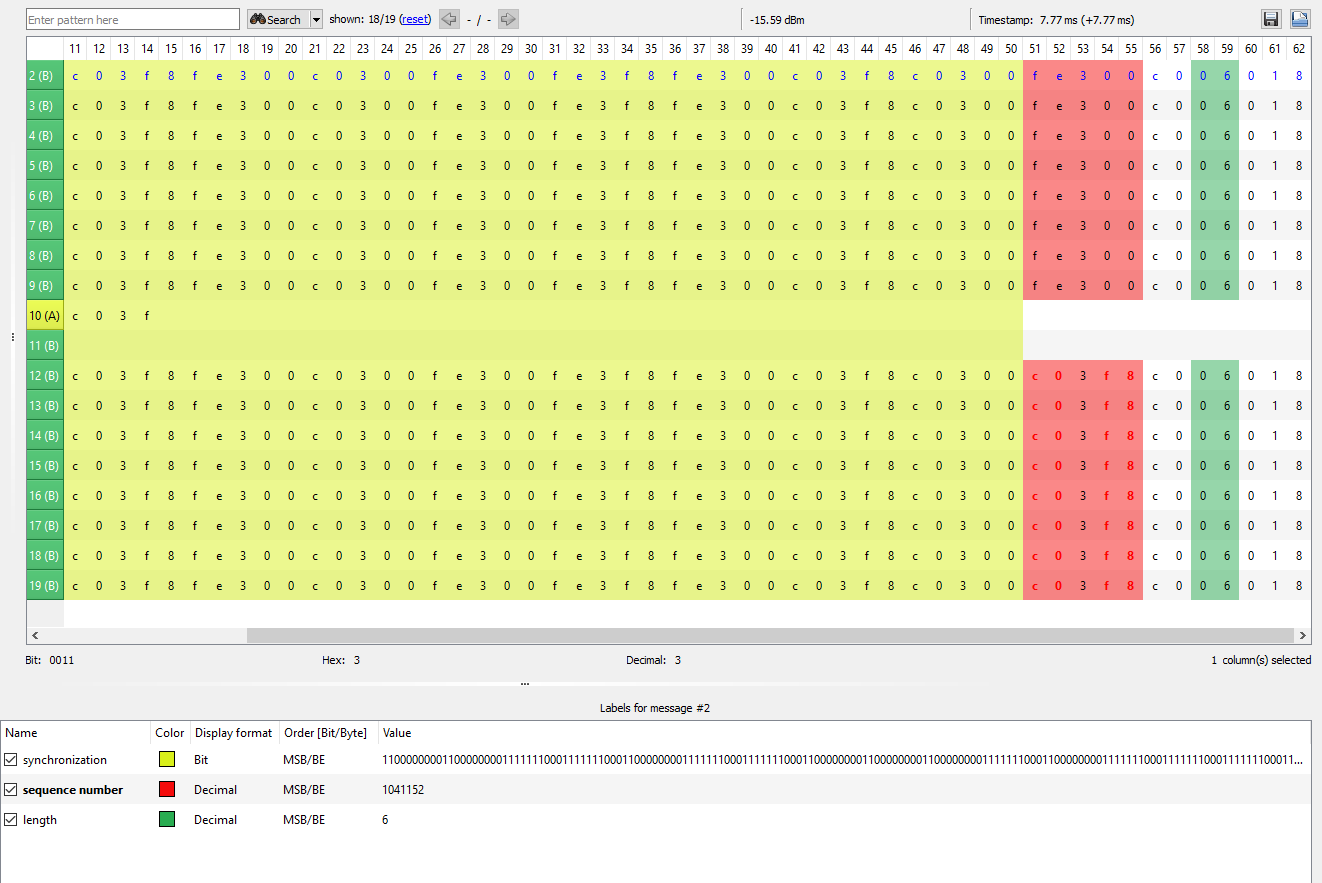
fe300andc03f8Analysis - Analysis Tab
- Moving over to the Analysis Tab the differences are highlighted showing the two different hex pairs
- Clicking on the Analyze Protocol Button it creates 3 labels for synchronization, sequence number and length
- Not quite sure if this breakout and assignment is correct or actually means anything….
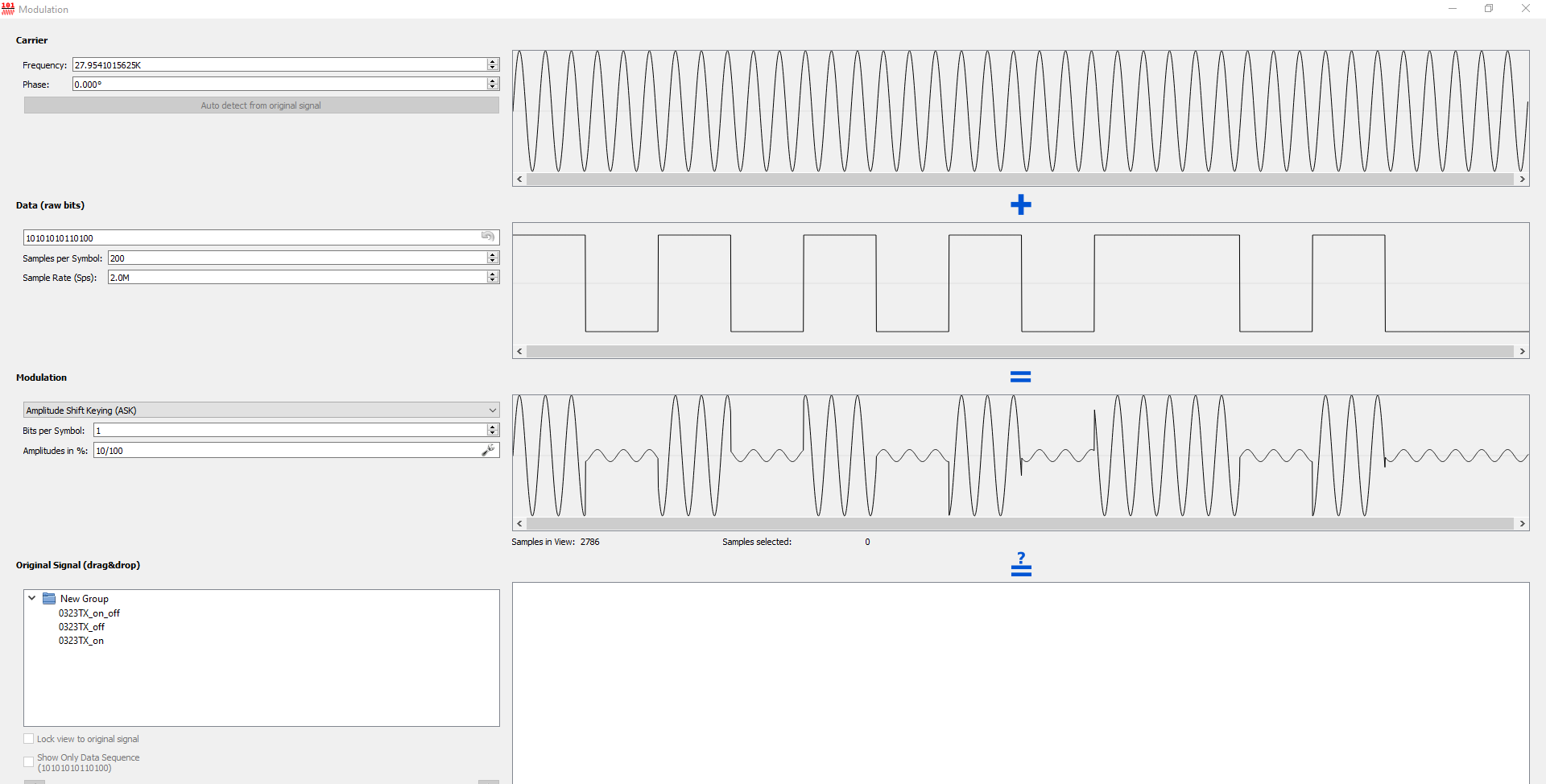
Analysis - Generator Tab
- Dragging the on_off signal into the generator tab to try to create our own signal vs just replaying the captured signal
- It successfully turns the outlet on and off
Pair Signal
- Repeating the same steps as above to capture and analyze the pair signal for the
0323transmitter
Breakout Analysis
- Trying to just visual and understand the differences…
- ON (0323)
c0300fe3f8c03f8fe300c0300fe300fe3f8fe300c03f8c0300fe300c0300cfe300unique symbols »fe00
- OFF (0323)
c0300fe3f8c03f8fe300c0300fe300fe3f8fe300c03f8c0300c03f8c0300cc03f8unique symbols »c0f8
- PAIR (0323)
c0300fe3f8c03f8fe300c0300fe300fe3f8fe300c03f8c0300fe3f8c0300cfe3f8unique symbols »fef8
Repeat with other transmitter
Repeat with 0623 Transmitter
- Captured the on, off and pairing signals and walked through the same steps as above to break down to the anlaysis tab.
- Differences in analysis tab show entire sequence is different and not just the 4 hex values above. Samples/Symbol were also set to 300 vs 200 on the 0323 transmitter… think I’m definetly just making stuff up…
- ON (0623)
c01fc7f1fc7f1fc7f180c060301fc60301fc7f180fe3f8c07f180180c06
- OFF (0623)
c01fc7f1fc7f1fc7f180c060301fc60301fc7f180fe3f8c0603f8180c06
- PAIR (0623)
c07f1fc7f1fc7f1fc6030180c07f180c07f1fc603f8fe301fc7f180c06
0623 Table [on>off>pair]
1
2
3
c07f1fc7f1fc7f1fc6030180c07f180c07f1fc603f8fe301fc6030180c
c07f1fc7f1fc7f1fc6030180c07f180c07f1fc603f8fe30180fe30180c
c07f1fc7f1fc7f1fc6030180c07f180c07f1fc603f8fe301fc7f180c06
- Last 10 hex values differ
0323 Table [on>off>pair]
1 2 3
c0300fe3f8c03f8fe300c0300fe300fe3f8fe300c03f8c0300fe300c0300c c0300fe3f8c03f8fe300c0300fe300fe3f8fe300c03f8c0300c03f8c0300c c0300fe3f8c03f8fe300c0300fe300fe3f8fe300c03f8c0300fe3f8c0300c
Both [0323 then 0623]
1
2
3
4
5
6
c0300fe3f8c03f8fe300c0300fe300fe3f8fe300c03f8c0300fe300c0300c
c0300fe3f8c03f8fe300c0300fe300fe3f8fe300c03f8c0300c03f8c0300c
c0300fe3f8c03f8fe300c0300fe300fe3f8fe300c03f8c0300fe3f8c0300c
c07f1fc7f1fc7f1fc6030180c07f180c07f1fc603f8fe301fc6030180c
c07f1fc7f1fc7f1fc6030180c07f180c07f1fc603f8fe30180fe30180c
c07f1fc7f1fc7f1fc6030180c07f180c07f1fc603f8fe301fc7f180c06
Final Thoughts
- First time trying to walk through this with universal hacker radio.
- I have really no idea what I’m doing… but able to replay raw signals and generate signals based on the message breakdowns
- I don’t understand what is going on inside the data itself and while there appear to be patterns they dont immediately pop out as an “aha that 0323 or 0623 transmitter!”
- More thoughts and analysis required for sure….